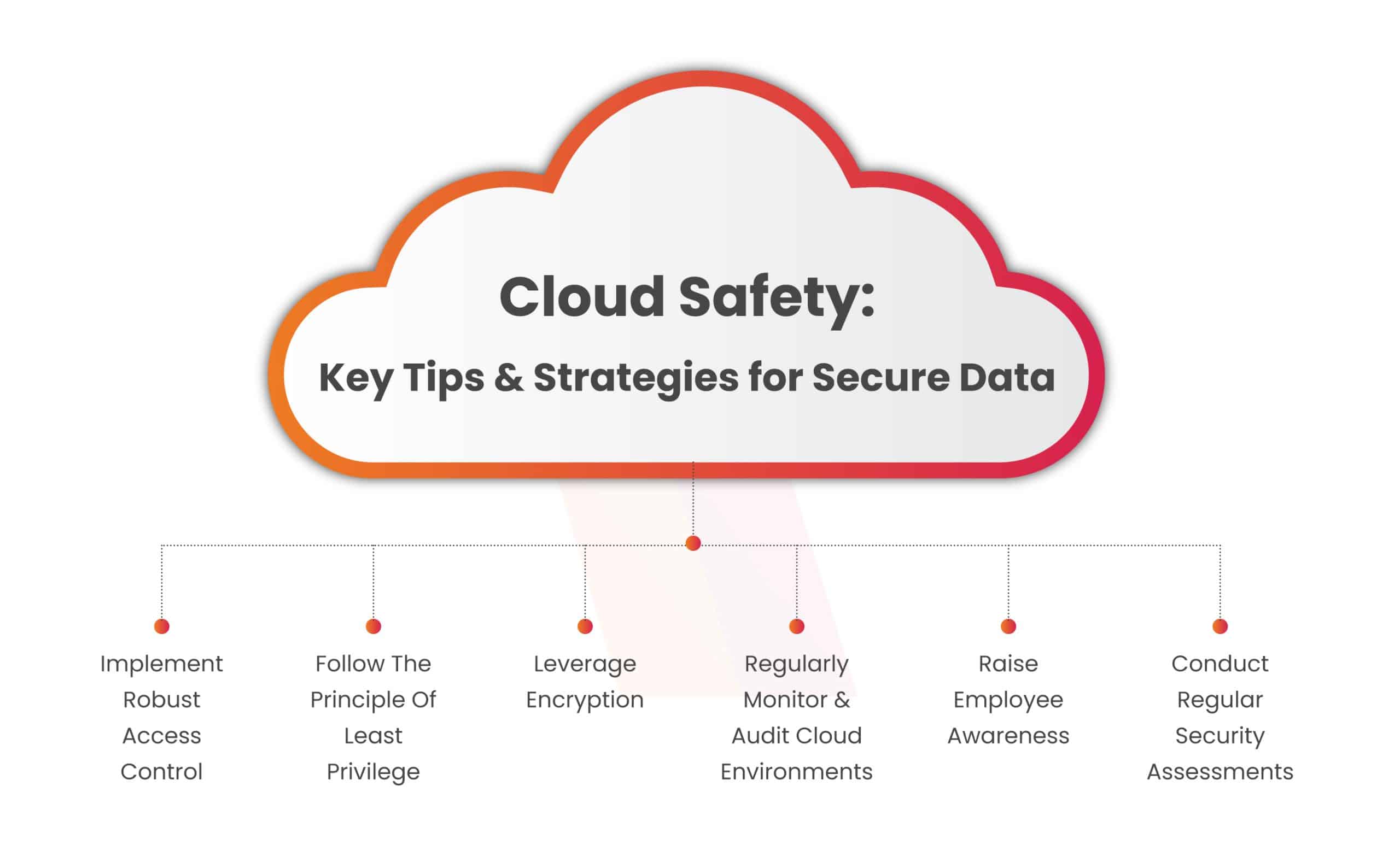
Kathmandu-The increasing trend of storing important files and data in cloud services has revolutionized how we manage information. However, as cloud service businesses expand rapidly, numerous security challenges have emerged alongside these benefits. Understanding comprehensive cloud security tips has become essential for protecting valuable digital assets.
Users cannot simply assume their data is completely safe after uploading to cloud services. Implementing proper cloud security tips requires vigilance and proactive measures to protect against various cyber threats and data breaches.
1. Maintain Regular Backups of Critical Data
Local Storage Backup Strategy
One of the most fundamental cloud security tips involves maintaining regular backups of important data on local storage devices or external hard drives. This practice protects against significant losses during data breach incidents when cloud data may be wiped out or locked down.
Backup Benefits:
- Protection during cloud service outages
- Continued workflow access without cloud connectivity
- Recovery options during data breach incidents
- Reduced dependency on single storage solutions
Electronic Copy Management
Developing habits for maintaining electronic copies ensures data accessibility even when cloud data is compromised or lost. This redundancy strategy represents a cornerstone of effective cloud security tips implementation.
Regular backup schedules help maintain data integrity and provide peace of mind knowing that critical information remains accessible through multiple channels.
2. Avoid Storing Sensitive Information in Cloud Services
Privacy Concerns in Digital Age
In today’s internet era, privacy issues have become increasingly serious concerns. This makes careful consideration of confidential file storage one of the most critical cloud security tips for protecting personal and business information.
High-Risk Information Categories:
- Online account passwords
- Credit card numbers and financial details
- National identification numbers
- Home addresses and personal locations
- Confidential business documents
Safe Cloud Storage Practices
Following proper cloud security tips means storing only files that require frequent access and avoiding highly sensitive personal identification information. If storing such information becomes necessary, always encrypt documents before uploading.
Current incidents of personal identity theft occur frequently, making selective cloud storage practices essential for maintaining digital security.
3. Use Cloud Services with Built-in Encryption Capabilities
Encryption-Enabled Cloud Platforms
Selecting cloud services that offer data encryption represents one of the most effective cloud security tips for protecting privacy. These platforms provide enhanced security and are considered more trustworthy for storing important information.
Encryption Benefits:
- Enhanced data protection during transmission
- Reduced unauthorized access risks
- Automatic security protocol implementation
- Professional-grade security standards
Decryption Access Requirements
Encrypted cloud services require decryption processes for data access, adding security layers that protect against unauthorized intrusion attempts. This additional step strengthens overall cloud security tips implementation.
4. Encrypt Data Before Cloud Upload
Third-Party Encryption Tools
When cloud services don’t provide built-in encryption, implementing cloud security tips includes using third-party encryption tools for enhanced protection. Cloud protection applications can be downloaded to apply passwords and secret key sequences before file uploads.
Pre-Upload Encryption Process:
- Download reliable cloud protection applications
- Apply password protection to files
- Generate secret key sequences
- Encrypt files before cloud transfer
- Maintain encryption keys securely
Double Protection Strategy
Even when using encrypted cloud services, personally encrypting files before upload provides additional security confidence. This layered approach exemplifies advanced cloud security tips for maximum data protection.
5. Implement Strong Passwords and Two-Factor Authentication
Two-Factor Authentication Benefits
Enabling two-factor authentication represents crucial cloud security tips that require password verification for every login attempt. This system blocks unauthorized access attempts from unknown devices.
Authentication Security Features:
- Password requirement for each login
- Device verification processes
- Unauthorized access prevention
- Enhanced account protection protocols
Strong Password Requirements
Preventing unauthorized hacking and cracking attempts requires implementing robust password strategies as part of essential cloud security tips.
Password Best Practices:
- Combine uppercase and lowercase letters
- Include numbers and special symbols
- Regular password change habits
- Unique passwords for each account
- Password manager utilization
6. Never Share Passwords with Others
Password Sharing Risks
Sometimes users share data access with others, inadvertently sharing passwords along with files. This practice violates fundamental cloud security tips and significantly increases cloud data security risks.
Sharing Alternative Methods:
- Use built-in sharing features
- Create limited-access guest accounts
- Set specific permission levels
- Monitor shared access regularly
Account Security Maintenance
Maintaining password confidentiality ensures that cloud security tips remain effective and prevents unauthorized access through shared credentials.
7. Use Anti-Spyware and Security Software
System Protection Requirements
Using anti-spyware software for system and device security represents essential cloud security tips for comprehensive protection. Even with secure cloud service providers, device vulnerabilities can compromise data security.
Security Software Benefits:
- Bug and virus detection
- Penetration point prevention
- Account access protection
- System vulnerability scanning
Device Security Integration
Computer systems connected to cloud services can develop vulnerabilities that provide hackers with penetration points for account access. Implementing robust cloud security tips includes maintaining device-level security.
8. Close Documents After Use
Document Management Practices
Closing documents after use represents simple yet effective cloud security tips that reduce security vulnerabilities. Open documents increase virus transmission risks and document hacking possibilities.
Post-Usage Protocols:
- Immediate document closure after use
- Session logout procedures
- Browser cache clearing
- Temporary file removal
Reduced Vulnerability Windows
Keeping documents open unnecessarily extends vulnerability periods when malicious software can access or corrupt files.
9. Regular Software Updates and System Maintenance
Update Importance for Security
Devices contain numerous documents and personal information ranging from identifying emails to bank account details. This information proves valuable to cybercriminals and represents targets for various cloud security tips implementation.
Potential Threat Scenarios:
- Identity theft for criminal activities
- Dark web information sales
- Ransomware attacks and data encryption
- Financial fraud and account compromise
Ransomware Protection
In ransomware attack situations, criminals may encrypt user data and demand payment for decryption. Regular software and operating system updates help prevent hacker system infiltration and maintain enhanced data security.
Update Benefits:
- Security patch installation
- Vulnerability closure
- Enhanced system protection
- Reduced attack surface areas
Comprehensive Security Strategy Implementation
Integrated Approach
Effective cloud security tips implementation requires combining multiple protective measures rather than relying on single security methods. This comprehensive approach addresses various threat vectors and provides robust protection.
Continuous Vigilance
Cloud security represents an ongoing process requiring regular attention and updates to maintain effectiveness against evolving cyber threats.
Risk Assessment
Regular evaluation of security practices ensures that cloud security tips remain current and effective against new threats and vulnerabilities in the digital landscape.
Following these comprehensive cloud security tips helps protect valuable data while enjoying the convenience and accessibility that cloud services provide. Security consciousness and proactive measures ensure that cloud technology benefits outweigh potential risks.





















Comments